-
You MUST read the Babiato Rules before making your first post otherwise you may get permanent warning points or a permanent Ban.
Our resources on Babiato Forum are CLEAN and SAFE. So you can use them for development and testing purposes. If your are on Windows and have an antivirus that alerts you about a possible infection: Know it's a false positive because all scripts are double checked by our experts. We advise you to add Babiato to trusted sites/sources or disable your antivirus momentarily while downloading a resource. "Enjoy your presence on Babiato"
Malware Scanner - Malicious Code Detector 1 January 2024 – Version 2.2
No permission to download
- Thread starter patrocle
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
patrocle updated Malware Scanner - Malicious Code Detector with a new update entry:
18 September 2021 – Version 1.6
Read the rest of this update entry...
@patrocle what is the password bro?
the password is in patrocle footer post in red@patrocle what is the password bro?
The easy way you use virustotal.comhow do you do scan php files?
The hard and fun way you build up your own scanner based on VirusTotal
Starting here:
GitHub - VirusTotal/yara: The pattern matching swiss knife
The pattern matching swiss knife. Contribute to VirusTotal/yara development by creating an account on GitHub.
GitHub - iomoath/yara-scanner: YaraScanner is a threat hunting tool, based on Yara Rules.
YaraScanner is a threat hunting tool, based on Yara Rules. - GitHub - iomoath/yara-scanner: YaraScanner is a threat hunting tool, based on Yara Rules.
Having all setup you can scan your files and generate a report like this:
YaraScanner - Scan Report
2023-04-18 14:57:16
| File Path | Rules Matched | Yara Rules |
1 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Documentation/assets/img/logo.jpg | [VMWare_Detection] | suspicious_strings.yar |
2 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Documentation/assets/img/logo.jpg | [vmdetect] | antidebug_antivm.yar |
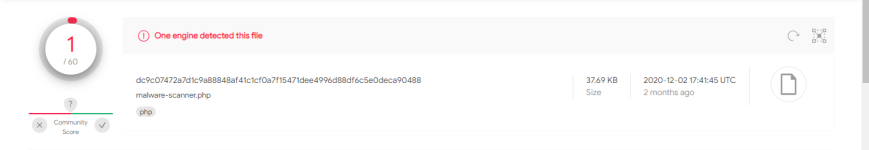
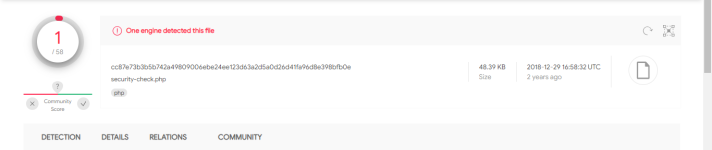
3 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/security-check.php | [Misc_Suspicious_Strings] | suspicious_strings.yar |
4 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php] | thor-webshells.yar |
5 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [IronTiger_ASPXSpy] | APT_Irontiger.yar |
6 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [Misc_Suspicious_Strings] | suspicious_strings.yar |
7 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [IDDQD_Godmode_Rule] | 1-GODMODE-RULE.yar |
8 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [possible_includes_base64_packed_functions] | javascript_exploit_and_obfuscation.yar |
9 | /media/usb/TEMP/malware-scanner.v2.1-4-18-2023/Source/malware-scanner.php | [r57shell_php_php, Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php] | WShell_THOR_Webshells.yar |
Cheers
shell-scanner.zip, contains a virus so the upload was canceled: {HEX}php.cmdshell.fx29.269.UNOFFICIAL FOUND
It's false, find this line on malware-scanner.php but it's for detect potential codes....
PHP:
$Patterns = array(
array(
'preg_replace\s*\(\s*[\"\']\s*(\W)(?-s).*\1[imsxADSUXJu\s]*e[imsxADSUXJu\s]*[\"\'].*\)', // [0] = RegEx search pattern
'PHP: preg_replace Eval', // [1] = Name / Title
'Detected preg_replace function that evaluates (executes) matched code. ' . 'This means if PHP code is passed it will be executed.', // [2] = description
'Part example code from http://sucuri.net/malware/backdoor-phppreg_replaceeval'
), // [3] = More Information link
array(
'c999*sh_surl',
'Backdoor: PHP:C99',
'Detected the "C99 Shell"? Backdoor that allows attackers to manage (and ' . 'reinfect) your website remotely. It is often used as part of a ' . 'compromise to maintain access to the hacked sites.',
'http://sucuri.net/malware/backdoor-phpc99045'
),
array(
'preg_match\s*\(\s*\"\s*/\s*bot\s*/\s*\"',
'Backdoor: PHP:R57',
'Detected the "R57 Shell"? Backdoor that allows attackers to access, modify and ' . 'reinfect your site. It is often hidden in the filesystem and hard to ' . 'find without access to the server or logs.',
'http://sucuri.net/malware/backdoor-phpr5701'
),
array(
'eval[\s/\*\#]*\(stripslashes[\s/\*\#]*\([\s/\*\#]*\$_(REQUEST|POST|GET)\s*\[\s*\\\s*[\'\"]\s*asc\s*\\\s*[\'\"]',
'Backdoor: PHP:GENERIC',
'Detected a generic backdoor that allows attackers to upload files, delete ' . 'files, access, modify and/or reinfect your site. It is often hidden ' . 'in the filesystem and hard to find without access to the server or ' . 'logs. It also includes uploadify scripts and similars that offer ' . 'upload options without security. ',
'http://sucuri.net/malware/backdoor-phpgeneric07'
),
/*array('https?\S{1,63}\.ru',
'Russian URL',
'Detected a .RU domain link, as there are many attacks leading the innocent visitors to .RU pages. Maybe it\'s valid link, but leave it to you to check this out.',
),*/
array(
'preg_replace\s*\(\s*[\"\'\”]\s*/\s*\.\s*\*\s*/\s*e\s*[\"\'\”]\s*,\s*[\"\'\”]\s*\\x65\\x76\\x61\\x6c',
'Backdoor: PHP:Filesman:02',
'Detected the “Filesman Shell”? Backdoor that allows attackers to access, modify ' . 'and reinfect your site. It is often hidden in the filesystem and hard ' . 'to find without access to the server or logs.',
'http://sucuri.net/malware/backdoor-phpfilesman02'
),
array(
'(include|require)(_once)*\s*[\"\'][\w\W\s/\*]*php://input[\w\W\s/\*]*[\"\']',
'PHP:\input include',
'Detected the method of reading input through PHP protocol handler in ' . 'include/require statements.'
),
array(
'data:;base64',
'data:;base64 include',
'Detected the method of executing base64 data in include.'
),
array(
'RewriteCond\s*%\{HTTP_REFERER\}',
'.HTACCESS RewriteCond-Referer',
'Your .htaccess file has a conditional redirection based on "HTTP Referer".' . 'This means it redirects according to site/url from where your visitors ' . 'came to your site. Such technique has been used for unwanted redirections ' . 'after coming from Google or other search engines, so check this directive carefully.'
),
array(
'jquery.min.php',
'Fake jQuery Malware',
'This file is infected with the Fake jQuery Malware. Removing the malware is not enough. Make sure your CMS and all its third-party components are up-to-date. All unused stuff should be ruthlessly deleted from server. Some of the compromised websites had malicious WordPress admin users with names like: backup, dpr19, loginfelix. Some of them had been created during past attacks though.'
),
array(
'GIF89a.*[\r\n]*.*<\?php',
'PHP file desguised as GIF image',
'Detected a PHP file that was most probably uploaded as an image via webform that loosely only checks file headers.'
),
array(
'\$ip[\w\W\s/\*]*=[\w\W\s/\*]*getenv\(["\']REMOTE_ADDR["\']\);[\w\W\s/\*]*[\r\n]\$message',
'Probably malicious PHP script that "calls home"',
'Detected script variations often used to inform the attackers about found vulnerable website.'
),
array(
'(?:(?:base64_decode|str_rot13)[\s\/\*\w\W\(]*){2,};',
'Multiple encoded, most probably obfuscated code found',
'This pattern could be used in highly encoded, malicious code hidden under ' . 'a loop of code obfuscation function calls. In most cases the decoded ' . 'hacker code goes through an eval call to execute it. This pattern is ' . 'also often used for legitimate purposes, e.g. storing configuration ' . 'information or serialised object data. '
),
/*array(
'<\s*iframe',
'IFRAME Element',
'Found IFRAME element in code. It\'s mostly benevolent, but often used ' . 'for bad stuff, so please check if it\'s a valid code.'
),*/
array(
'strrev[\s/\*\#]*\([\s/\*\#]*[\'"]\s*tressa\s*[\'"]\s*\)',
'Reversed string "assert"',
'Assert function name is being hidden behind strrev().'
),
array(
'is_writable[\s/\*\#]*\([\s/\*\#]*getcwd',
'Is the current DIR Writable?',
'This could be harmless, but used in some malware'
),
/*array('(?:\\\\x[0-9A-Fa-f]{1,2}|\\\\[0-7]{1,3}){2,}',
'At least two characters in hexadecimal or octal notation',
'Found at least two characters in hexadecimal or octal notation. It '
. 'doesn\'t mean it is malicious, but it could be code hidding behind '
. 'such notation.'),*/
array(
'\$_F\s*=\s*__FILE__\s*;\s*\$_X\s*=',
'SourceCop encoded code',
'Found the SourceCop encoded code. It is often used for malicious code
hidding, so go and check the code with some online SourceCop decoders'
),
array(
'(?:passthru|shell_exec|proc_|popen)[\w\W\s/\*]*\([\s/\*\#\'\"\w\W\-\_]*(?:\$_GET|\$_POST|\$_REQUEST)',
'Shell command execution from POST/GET variables',
'Found direct shell command execution getting variables from POST/GET,
which is highly dangerous security flaw or a part of malicious webrootkit'
),
/*array('\$\w[\w\W\s/\*]*=[\w\W\s/\*]*`.*`',
'PHP execution operator: backticks (``)',
'PHP execution operator found. Note that these are not single-quotes!
PHP will attempt to execute the contents of the backticks as a shell
command, which might indicate a part of a web rootkit'),*/
array(
'fsockopen\s*\(\s*[ \'\"](?:localhost|127\.0\.0\.1)[ \'\"]',
'Opening socket to localhost',
'Found code opening socket to localhost, it\'s worth investigating more'
),
array(
'fsockopen\s*\(.*,\s*[ \'\"](?:25|587|465|475|2525)[ \'\"]',
'Opening socket to known SMTP ports, possible SPAM script',
'Found opening socket to known SMTP ports, possible SPAM script'
),
array(
'(?:readfile|popen)\s*\(\s*[ \'\"]*\s*(?:file|http[s]*|ftp[s]*|php|zlib|data|glob|phar|ssh2|rar|ogg|expect|\$POST|\$GET|\$REQUEST)',
'Reading streams or superglobal variables with fopen wrappers present',
'Found functions reading data from streams/wrappers - please analyze the code'
),
array(
'array_(?:diff_ukey|diff_uassoc|intersect_uassoc|udiff_uassoc|udiff_assoc|uintersect_assoc|uintersect_uassoc)\s*\(.*(?:\$_REQUEST|\$_POST|\$_GET).*;',
'Callback function comming from REQUEST/POST/GET variable possible',
'Found possible local execution enabling-script receiving data from POST or GET requests'
),
/*array(
'^(((.*)(=|;)(\s*)?)|((@|\s)*))extract\s*\(',
'Extract Function',
'PHP extract function found. Extract creates variables from an array (eg $_POST, $_GET or $_REQUEST). It can be legit, but if there is some strange code execution like $extracted_variable_1($extracted_variable_2) it should be malicious.'
),*/
array(
'^(((.*)(=|;)(\s*)?)|((@|\s)*))(include|require)(_once)?\s*\(?("|\')https?://',
'Remote Include',
'Include or require which includes a remote file. It should be malicious, and vulnerable as well.'
),
array(
'\\\\x([abcdef0-9]{2}){3,}',
'Hex Encoded String',
'Code which is hex encoded. It can be legit, but not a usual thing. Malicious users can hide their functions in hex encoded expressions.'
)
);
$FileNames = array(
'Probably an OpenFlashChart library demo file that has known input ' . 'validation error (CVE-2009-4140)' => 'ofc_upload_image.php',
'Probably an R57 shell' => 'r57.php',
'Probably a C99 shell' => 'c99.php',
'Probably a C100 shell' => 'c100.php',
'PhpInfo() file? It is advisable to remove such file, as it could reveal too
much info to potential attackers' => 'phpinfo.php',
'PerlInfo() file? It is advisable to remove such file, as it could reveal too
much info to potential attackers' => 'perlinfo.php'
);@patrocle
@patrocle could you please update latest version
patrocle updated Malware Scanner - Malicious Code Detector with a new update entry:
v2.1 4/18/2023
Read the rest of this update entry...
@patrocle could you please update latest version
patrocle updated Malware Scanner - Malicious Code Detector with a new update entry:
1 January 2024 – Version 2.2
Read the rest of this update entry...
1 January 2024 – Version 2.2
1 January 2024 – Version 2.2 - Untouched
- Improved Dashboard page
- Improved Malware Scanner process
- Updated CSS & JS libraries
- Optimized source code (Performance Improvements)
- Fixed Bugs
Read the rest of this update entry...
Latest posts
-
-
-
-
GoBiz - Digital Business Card + WhatsApp Store Maker | SaaS | vCard Builder
- Latest: Charlie-wade